How to Tell if Someone is Accessing Your iPhone Remotely
iPhones are known for their security. Over the years, Apple has brought out regular updates and developments to ensure their users don’t have to worry about losing their personal data.
Despite these constant security improvements, iPhones aren’t immune to internet exploits. If cybercriminals can deploy these malicious items into your iPhones, they can potentially gain access to all your information.
Additionally, spyware can be remotely installed on your devices giving hackers complete control over your iPhone without even touching it.
The thought of someone spying on your iPhone is pretty scary. In this article, we have gathered up a few tested methods to detect and prevent hackers from accessing your iPhone remotely.
Table of Contents
How Can Someone Access Your iPhone Remotely?

Even after taking precautions like using passcodes or face locks, cybercriminals still have pretty interesting tricks up their sleeves.
1. Malicious Apps
Apple has a strict review process for what app makes it to their store. Still, hackers have been able to disguise their harmful exploits in simple entertaining apps.
Once these apps are on your phone, they can access not only your personal information but even your camera and microphone. That’s why whenever apps ask you for permissions give it a good thought and then accept them.
Additionally, when installing apps even from the Play Store on Android devices it’s recommended to download from trusted sources with positive user reviews. Refrain from installing APK files if you’re not sure or don’t know exactly what you’re doing.
Similarly, stick to official apps on the App Store and don’t get IPA files unless confident.
2. Phishing
Phishing refers to the act of sending fake emails and misleading URLs to lure users into opening them or downloading harmful files. Usually, these messages are made to look like they are from reputable sources but in reality, are from cyber attackers.
Hence, if you ever get a message or email asking you to open a specific URL or send them your information, don’t open these phishing links. Be cautious and avoid opening any suspicious links.
3. Hacked iCloud Account
iCloud is a direct link to everything that is on your iPhone. If your account details are compromised hackers can get access to your passwords, and settings, and even track you through “Find My iPhone.”

If you notice any strange behavior with your iCloud including passwords not working or strange login notifications, report it immediately, change your password and ideally log out of everything and only manually log back in into the most important devices.
Signs Your iPhone Is Being Accessed Remotely
If someone is remotely accessing your iPhone, there’s a good chance your phone will show one or more of these signs.
- Quick Battery Drainage: If your iPhone is suddenly running out of battery life more quickly than usual, it can be a sign that some malicious apps are running in the background.
- Higher Data Usage: If you’re noticing an unexpected increase in data usage that is because your iPhone is sending your information to the hacker’s phone.
- Phone Heats Up: Due to these harmful and resourceful background processes, most iPhones also show signs of heating up.
- Strange Pop-Ups: Although this one isn’t common if your iPhone is showing strange pop-ups, it’s certain that you have malware installed.
- Password and Account Changes: If you aren’t able to log in through your usual passwords, it’s an immediate red flag that someone has accessed your credentials.
- Performance Slowdown: Overall, if your phone is showing signs of laggy and slow performance then your phone is running more background apps than it can handle.
We also have a detailed guide on how to see if your phone is tapped that you should check out to learn more about the nuances of how hackers covertly get control of your phone and spy on you.
How to See Who Has Access to Your iPhone?
Now, let’s look at the ways you can determine if someone is accessing your iPhone secretly:
1. Check For Unauthorized Sign-ins
Within the settings, you can find all the devices connected to your iPhone. If you find a device that isn’t supposed to be there then follow these steps:
- Head to your iPhone’s settings and tap on your Apple ID.
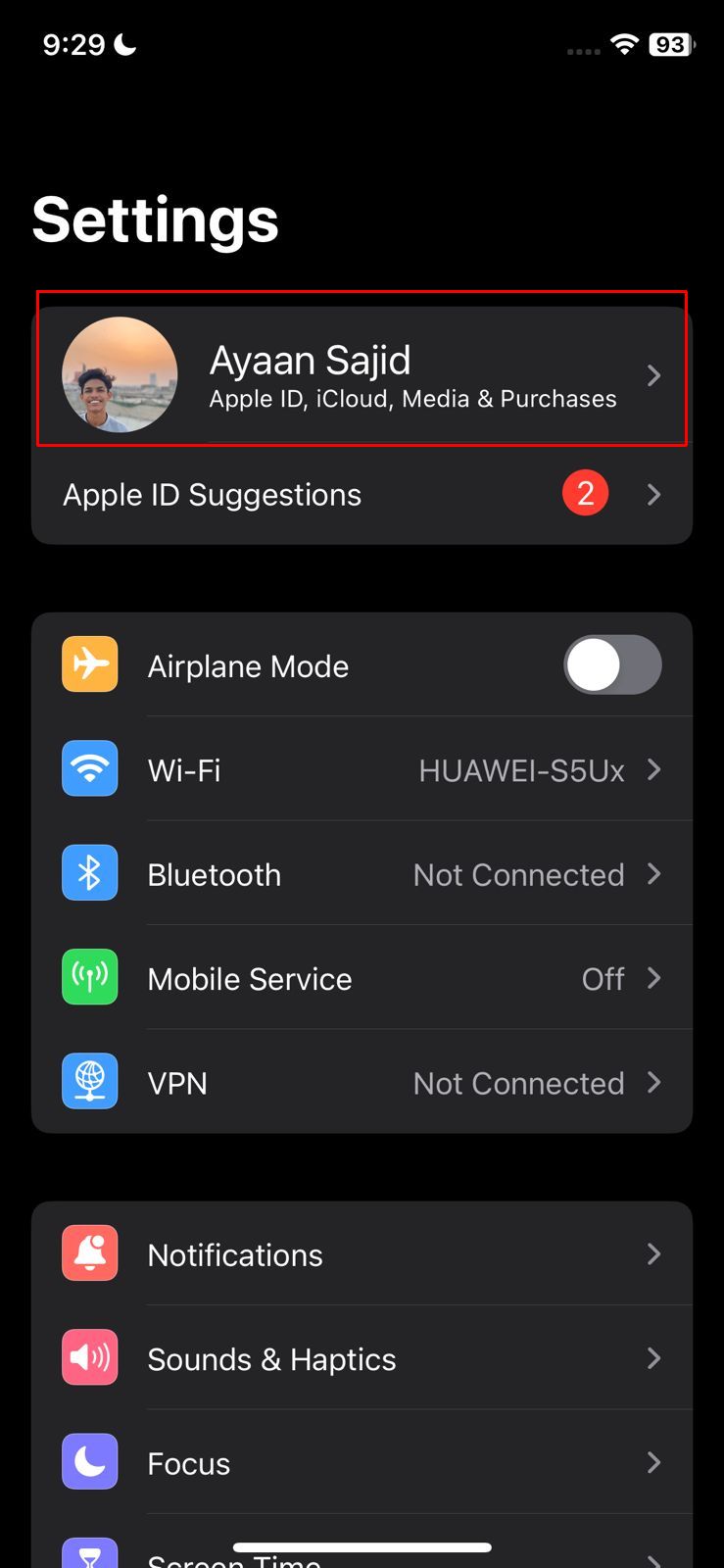
- Scroll down to the end and you’ll find all the devices connected to your Apple ID.
View your Devices - To remove a device just tap on the unknown device and select the “Remove from account” option.
2. Face or Touch ID Change
You can also verify whether there are any unexpected alternate Face ID profiles or extra fingerprints set up on your device by following these steps:
- Open the “Settings” on your iPhone
Choose Settings - Once you are in, scroll to the “Touch ID & Passcode.”
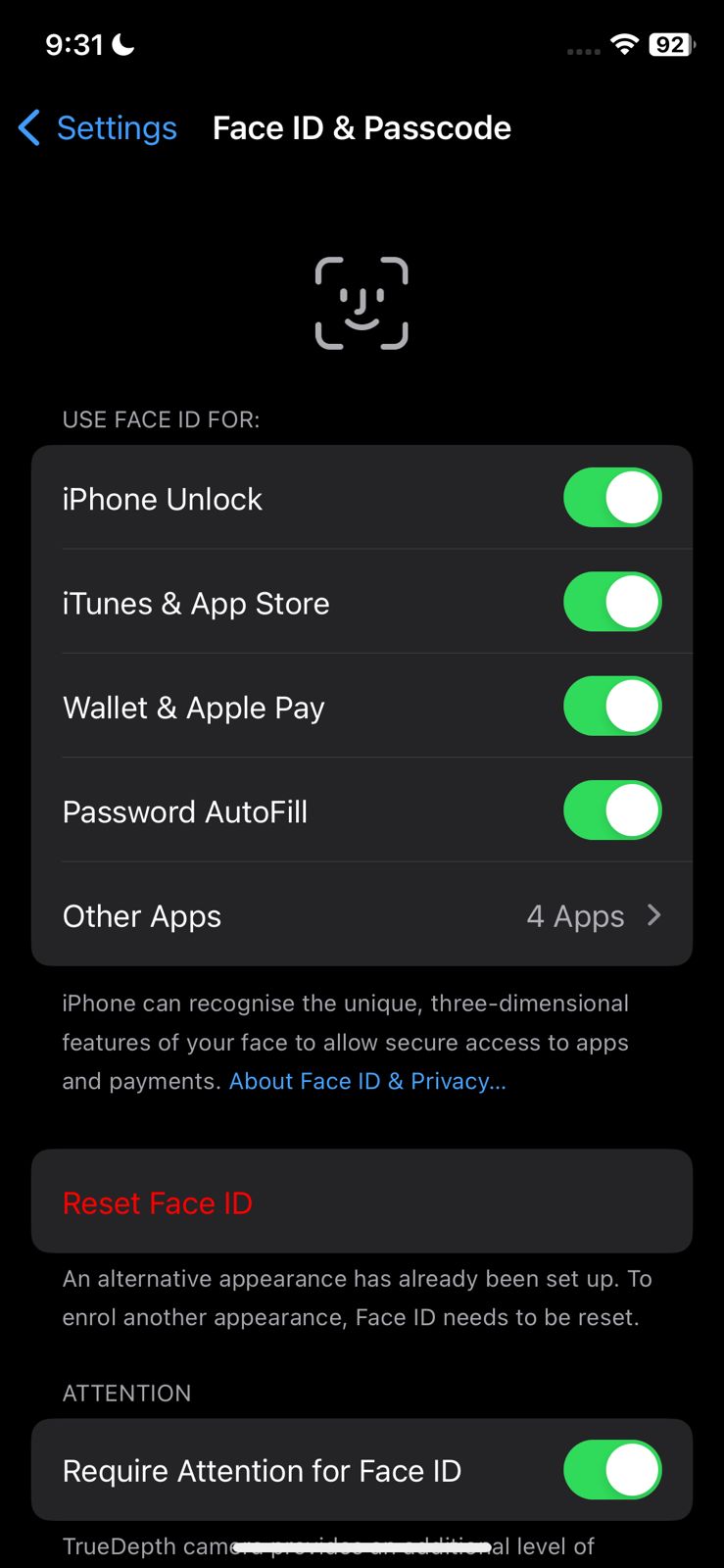
Look for un-recognized passcodes If you see any extra fingerprints or face IDs, tap on the “Reset Face ID” option to delete them.
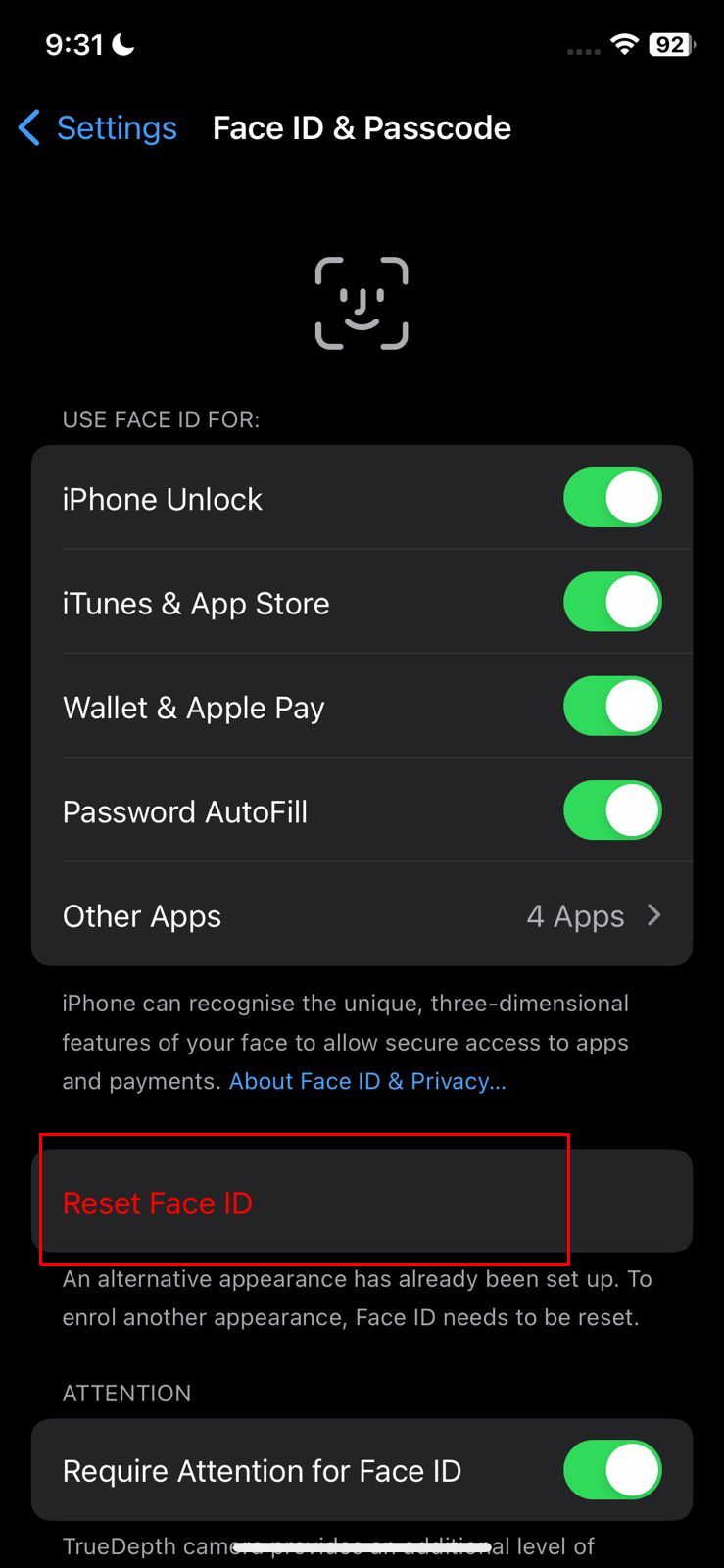
Tap Reset Face ID
After deleting your existing Touch or Face ID, replace them with newer and secure ones.
3. Two-Factor Authentication
If you’ve enabled two-factor authentication, take a look at your list of trusted devices to make sure you recognize all of them. If you haven’t enabled it yet, you can do so by following these steps:
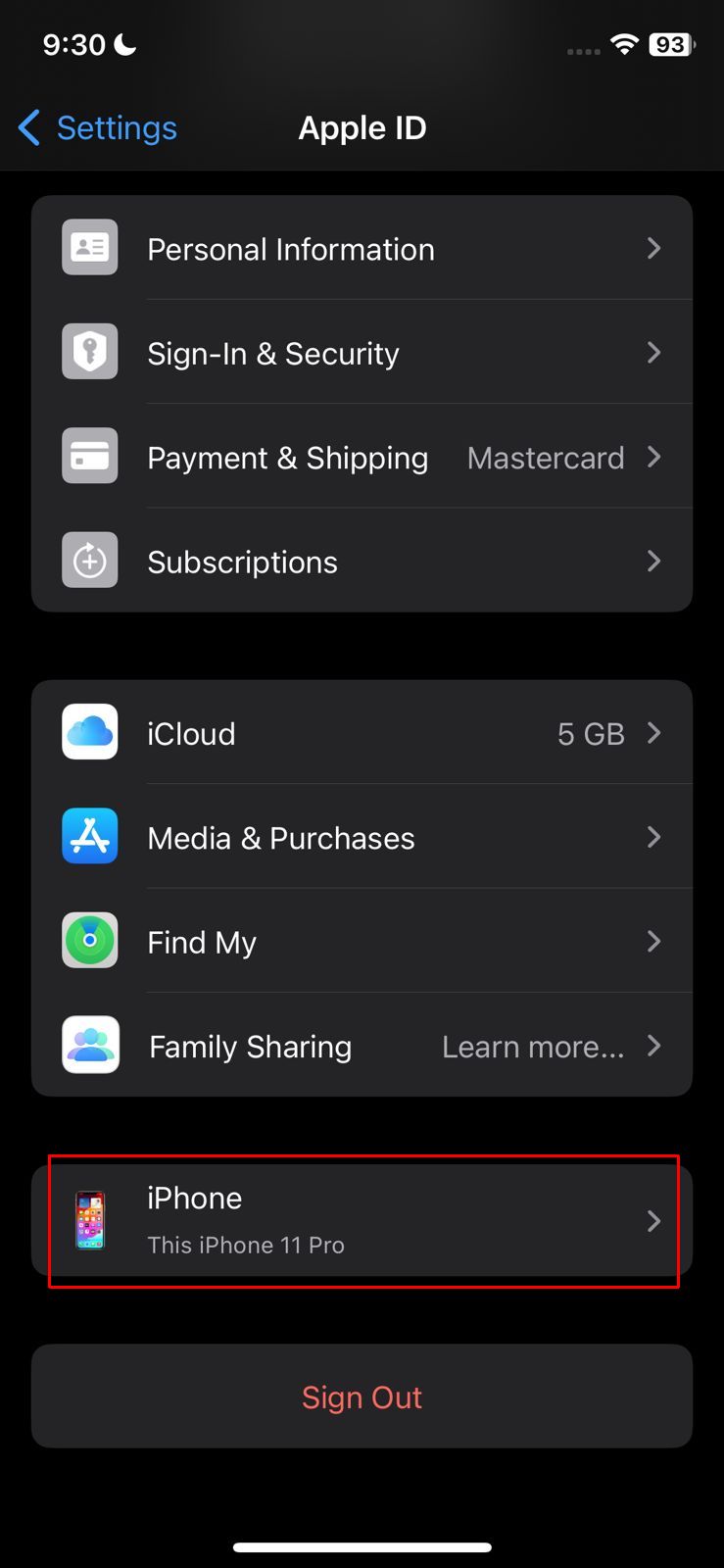
- Launch your iPhone’s settings and tap on your Apple ID.
Tap your Apple ID - Next, press the “Password & Security” option.
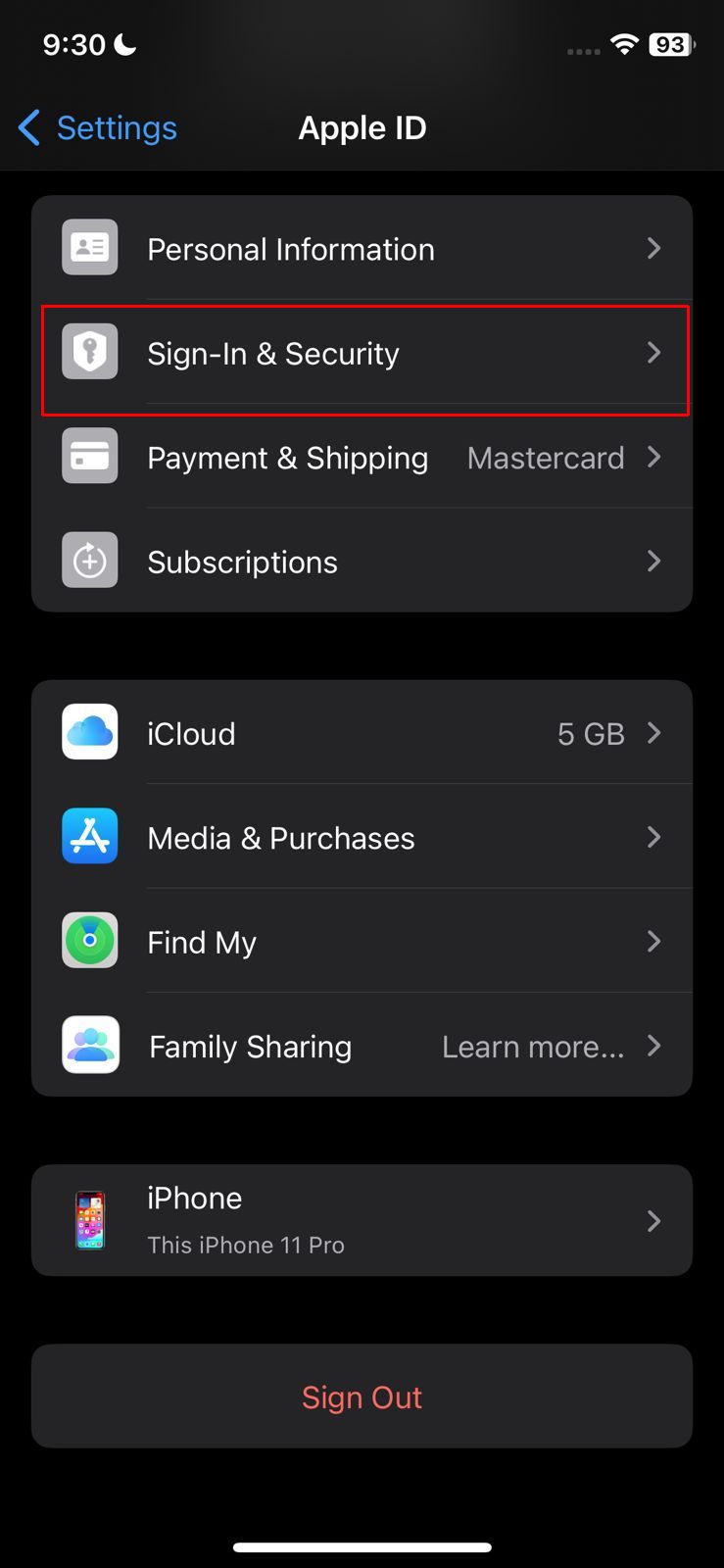
Go to sign in & security - Within the “Sign-In & Security” settings, enable the “Two-Factor Authentication” to receive an email or SMS every time someone tries to log into your device.
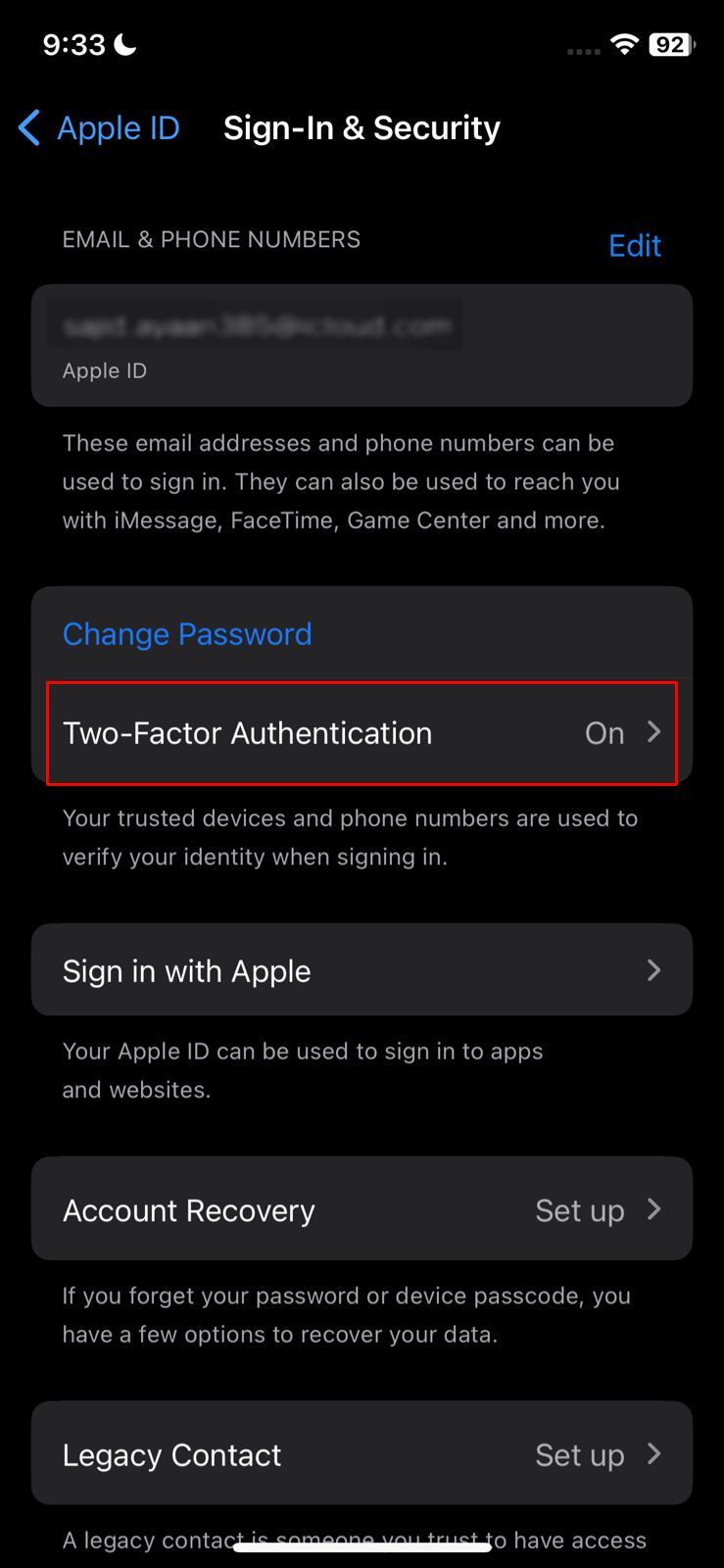
Enable Two-Factor Authentication
Carefully double-check authentication requests to ensure they aren’t from a device you didn’t authorize.
4. Monitoring Devices via Find My iPhone
Find My iPhone” is a built-in feature that helps in locating a lost or misplaced iPhone. However, it can also be a handy tool to detect unauthorized access.
When someone has your Apple ID credentials, they can potentially track your location through Find My iPhone or even play sounds, mark it as lost, or erase it. If someone is maliciously tracking you, you might notice your device unexpectedly playing the “Find My” sound or receiving a notification that your device has been marked as lost.
To check:
- Open the “Find My” app on another Apple device or access it via the web at iCloud.com.
- Check for any unfamiliar devices listed under your Apple ID. You will need to log in for this.
- If you notice any device that shouldn’t be there, consider it a red flag and immediately remove it.
Tips to Stop Someone From Accessing Your iPhone Remotely
Knowing the signs of being accessed remotely is one thing and preventing it from happening in the future again is another. Here are a few quick tips you should adopt to avoid hackers from accessing your iPhone remotely.
- Never leave your phone unattended
- Always use Two Factor Authentication (2FA) when possible
- Keep your apps and iOS versions up to date.
- Use strong and unique passwords for iCloud and Apple ID
- Never use public Wi-Fi without a VPN
- Be cautious of suspicious links and messages
- Always install apps from trusted sources.
- Review permissions for apps you use.
Conclusion
Mobile phones have become one of our most personal possessions. Yet, even if you have an iPhone you are at risk of falling into a cyber trap. And the best way to avoid being a victim of these is by keeping an eye on your iPhone. From monitoring the apps you download to your overall phone behavior, you can ensure that no one comes close to your iPhone.
FAQs
Antivirus software is effective in protecting your phone from various spyware. It can help detect and remove malware, provide protection against phishing, and much more.
While no device is safe from hackers, Apple iPhones are generally difficult for hackers to crack. Factors like automatic software updates, the high cost of hacking iPhones, and limited user customization options make iPhones the more secure choice.
VPNs can help guard against remote access on your iPhone by encrypting your internet connection and masking your IP address, making it more difficult for unauthorized parties to gain remote access to your device.
 Reviewed by
Reviewed by