What Risks Are You Taking When Signing in With Google?
In today’s digital era, managing multiple passwords for various websites and online services can be overwhelming and tricky. Reusing passwords across accounts increases vulnerability to hacking as well. Thankfully, using a Google account for sign-ins offers convenience, but it raises valid concerns about security at the same time.
The following guide will discuss a few possible risks associated when one signs in using Google credentials. But before that, let’s understand the tech behind log-in using Google.
Table of Contents:
What Happens When You Sign in with Google?
Standard practice dictates that you must first sign up for an account with a website before you can use it. To verify that you are human using your own identity and not a bot, most services will ask you to create (yet another) login and provide an email address to which they can send a confirmation message.
You can avoid this step altogether by signing in with Google on the site. You are instead dependent on the services themselves to verify your identity and handle your account. When you select the option to log in with your Google account on a website or application, a request is sent to the Google Sign-In service.
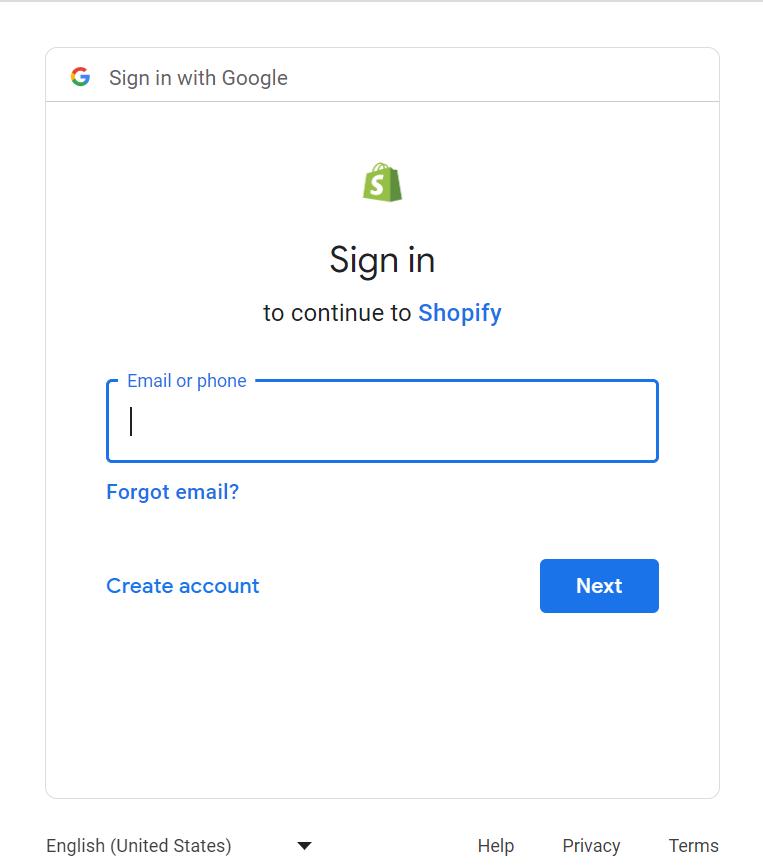
You are then redirected to the Google Sign-In page, where you are prompted to enter your Google account credentials, such as your email address and password.
After successful authentication, the website or application may request certain permissions to access your Google account information or perform specific actions on your behalf. This could include accessing your basic profile information, contacts, or even the ability to manage your Google Calendar or send emails.
After verifying the user’s identity, Google returns an authentication token confirming that the user is the one they claimed to be. The website receives the authorization code and sends it to Google’s servers for verification.
Once the code is validated, the website or application receives an access token. This confirms your identity and grants you access to the requested services or features.
For any future attempts at exploring the website, you just need to sign-in with your Google account. Since most people already have their Google account signed in, Google just shows a pop-up on the website, and one-click login feature allows access to the website.
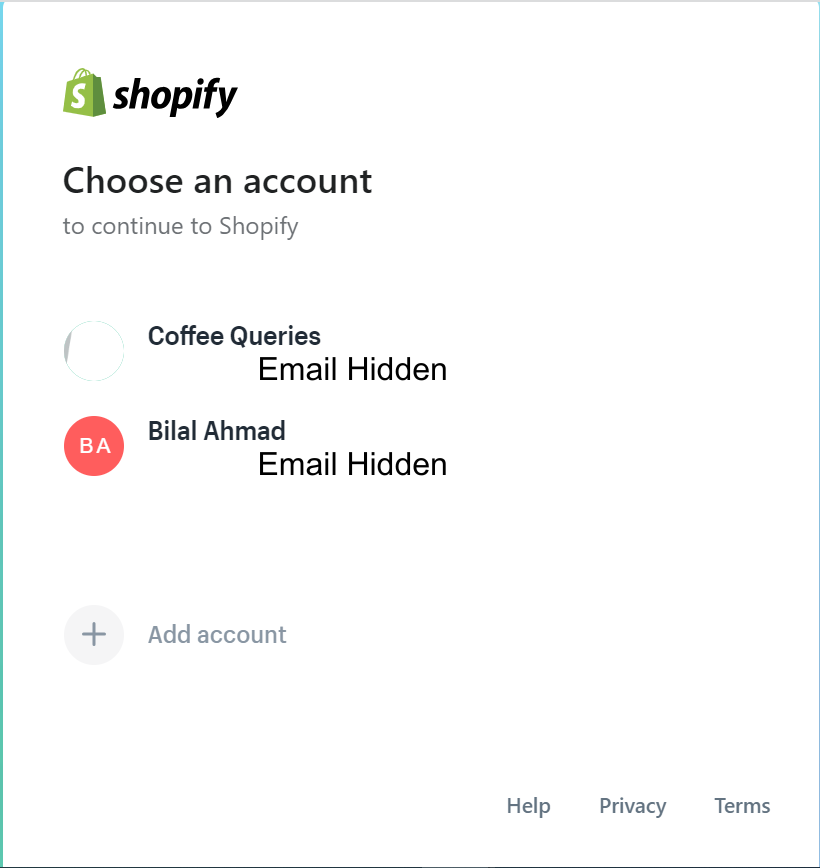
Now you can explore the site at your leisure.
With Google, you can limit who sees what you post and how often. Keep in mind that declining permission can render certain services inoperable as well.
Pros of Signing with Google
Using Google to sign-in brings an array of benefits for the users.
1. Convenience and Easy Access
When you sign in using your Google account, you can easily switch between different services. You will not need to sign up for anything new, complete any complicated forms, or remember any usernames or passwords. It just takes a few seconds to sign in with your Google account and begin using the app.

Signing in with your Google account also enables you to sync your information across many devices. Using the same Google account across your smartphone, laptop, and tablet ensures instantaneous access to your information without the need for manual syncing. This facilitates a more streamlined and efficient user experience.
2. Single Sign-on
Google’s single sign-on feature allows you to use your Google account to log in to multiple applications, saving time and reducing the need to remember multiple passwords. This streamlined process enhances security and simplifies account access management in case of lost devices or forgotten passwords.

3. Google’s Security
Most websites lack the financial means to spend as much on security as Google. Alternatively, you should consider whether or not you feel secure entrusting the website in question with your personal data. You probably trust Google more than an unknown, smaller website to accomplish this.
One significant advantage of using Google Sign-In is that the website or application you’re accessing doesn’t have access to your actual password. Instead, they receive a token that verifies your Google account, without exposing your personal information. This means that even if the website experiences a security breach, there is no real account for your data to be compromised within their system.

You can always withdraw their token and prevent them from accessing your data, regardless of whether the website is hacked or you decide to quit. In comparison to the account management system used by the average website user, which cannot often remove accounts, this is a major benefit.
Risks of Signing with Google
Now, while there are quite a few benefits associated with signing in with Google, there are certain risks which most people overlook.
1. All Linked Accounts Can Be Compromised if Your Google Account is Hacked
One significant risk of using a Google account as a sign-in method for non-Google websites is that if your Google account is hacked or compromised, it can potentially lead to the compromise of all linked accounts.
When you use your Google account as a master passphrase to access multiple non-Google websites, it means that your Google password serves as the key to unlock all of these accounts. If hackers access your Google account, they can navigate to the account’s settings, where they may find a list of connected services or websites.
If you think about it, this gives endless possibilities and access to a hacker. This is a major risk for a user who has their Google account connected with numerous important applications.
2. What if Google Goes Down?
While the chances of this event are thin, the possibility cannot be completely neglected.
In the event of an extended outage or disruption of Google services, users may not only lose access to Google itself but also to any other websites that rely on Google for authentication.
Over the course of several years, Google has experienced significant service disruptions in multiple episodes. These incidents occurred in 2013, 2014, 2018, 2020, and 2022 resulting in widespread outages across various Google services. The disruptions had an adverse impact on users who rely on Google’s platforms for their daily activities and business operations.
What this indicates is the fact that even the bigger tech giants, like Facebook, or Google are not completely safe from any such problems. As a matter of fact, bigger companies may sometimes take too long to have their servers fixed.
3. What if Your Google Account Can Gets Suspended
In some cases, Google may suspend or terminate an account due to violations of their terms of service or suspicious activities. If this happens, you will lose access to all the websites and services connected to your Google account, causing disruption and potential loss of data or functionality.
Another case is if you forget your Google account password or face issues with the account recovery process, you may be locked out of your account. This means you won’t be able to access any websites or services that rely on your Google account for authentication until the issue is resolved, which can be a time-consuming and potentially frustrating process.
As a result of either of those issues, what’s compromised even more is your access to the third-party Non-Google website.
4. Your Information is Accessible to Third-Party Sites
When using Google Sign-In, you grant the website access to certain information from your Google account, such as your basic profile details, email address, and potentially other permissions. This raises concerns about data privacy, as the website may collect and store this information, potentially sharing it with third parties without your knowledge or consent.
There is no way to retrieve information once it has been sent to a third-party service. Your friends’ privacy may potentially be at risk without your knowledge. The following are some examples of the information that various sites may access from your Google account:
- Contacts
- To-do list; planner; timetable etc
- Google Wallet
- Your Birthday
- Your social media profiles
For example, a website might request access to your Google Calendar, contacts, or even the ability to send emails on your behalf. By granting these permissions, you are essentially allowing the website to access and utilize that specific information from your Google account.
Besides, the website receiving your Google account information could store this data within their own systems and share it with other third-party entities without your explicit knowledge or consent.
5. Google’s Terms and Policies Can Change
Most people don’t read the fine print of policies by Google or other companies. Many users simply accept the terms and conditions without fully grasping the extent of their implications. This lack of awareness can leave individuals unaware of how their data is being used and shared by Google and its partner websites and applications.
Therefore, the question arises: What if Google changes the terms and policies some day which gives any loophole access to hackers. Again, the chances of such an occurrence are thin, since Google is quite strongly focused on security. However, they cannot be entirely neglected as even today, tech giants including Google are facing numerous security issues.
6. Risk of a Phishing Attack?

Phishing attacks continue to pose a significant threat, and it’s important to exercise caution when using Google as an authentication method, especially on potentially fraudulent websites.
Let’s consider a scenario where a website promises large sums of money without any upfront investment, which is a classic red flag for a scam. However, despite the warning signs, many individuals still fall victim to these schemes.
In such cases, the website may prompt you to authenticate with Google, leading you to a page that appears identical to the genuine Google Sign-In page. This is a textbook example of a phishing attack, where cybercriminals attempt to trick you into disclosing your Google email and password. Unfortunately, as soon as you submit this information on the fake form, it lands directly in the hands of hackers.
In 2019, 65% of American businesses experienced effective phishing attacks. This highlights the critical need for vigilance when it comes to using Google as an authentication method, particularly on unfamiliar or suspicious websites.
Our Recommendation

The utilization of Google as an authentication method for other applications carries certain risks, but it remains one of the most convenient and secure approaches available, so far.
Google has made significant strides in enhancing security measures and addressing vulnerabilities. They have implemented features like two-factor authentication, which adds an additional layer of protection by requiring a verification code in addition to your password.
Furthermore, Google’s advanced security systems include measures such as new location login notifications, which alert you if someone tries to access your account from an unfamiliar location, and mobile-based authentication for added security when logging in from different devices.
It’s also important to note that Google invests heavily in securing user accounts and employs sophisticated algorithms to detect and prevent unauthorized access. They continuously monitor for suspicious activities, such as login attempts from unfamiliar locations or devices, and prompt additional verification steps to ensure the account owner’s identity.
It is worth noting that in 2018 Sundar Pichai, the CEO of Google, was called to testify before Congress to address concerns related to data privacy and potential anticompetitive practices. “Sundar Pichai’s testimony emphasized Google’s commitment to user privacy, transparency, and control over personal data. He highlighted investments in privacy measures, restricted third-party access, and addressed concerns about data protection and competition.”

Comparing the security measures implemented by Google with those of average websites, it becomes evident that Google provides a significantly higher level of security. Therefore, considering the combination of convenience and robust security measures offered by Google Sign-In, it remains the recommended choice for users seeking an efficient and secure authentication method.
Ask Yourself!
While signing in with Google can speed up the process of accessing applications, doing so raises worries about the user’s privacy and security. Think about the following before deciding whether or not to use your Google account:
- What is the importance of privacy to you?
- Is it safe to join up for this new service?
- Which details are you willing to reveal?
- Will you need a Google account to use this software, or will it work without it?
Signing in with Google is not the ideal choice for you if you value privacy and want more control over your data. Using Google credentials is convenient if you are already familiar with Google and trust the app or website you are signing up for.
How to Remove Google-Sign in on a Third-Party Website?
After reading this guide, many of you might decide to not use your Google account anymore as a preferred mode of sign-in. Therefore, if you wish to revoke Google account access to certain websites, applications, or even all of them, follow this simple procedure.
Step 1: Access Your Google Account
The first step is to access your Google account by going to accounts.google.com. Enter your email and password over here. In case you are already logged in, you’ll be shown a screen like this.
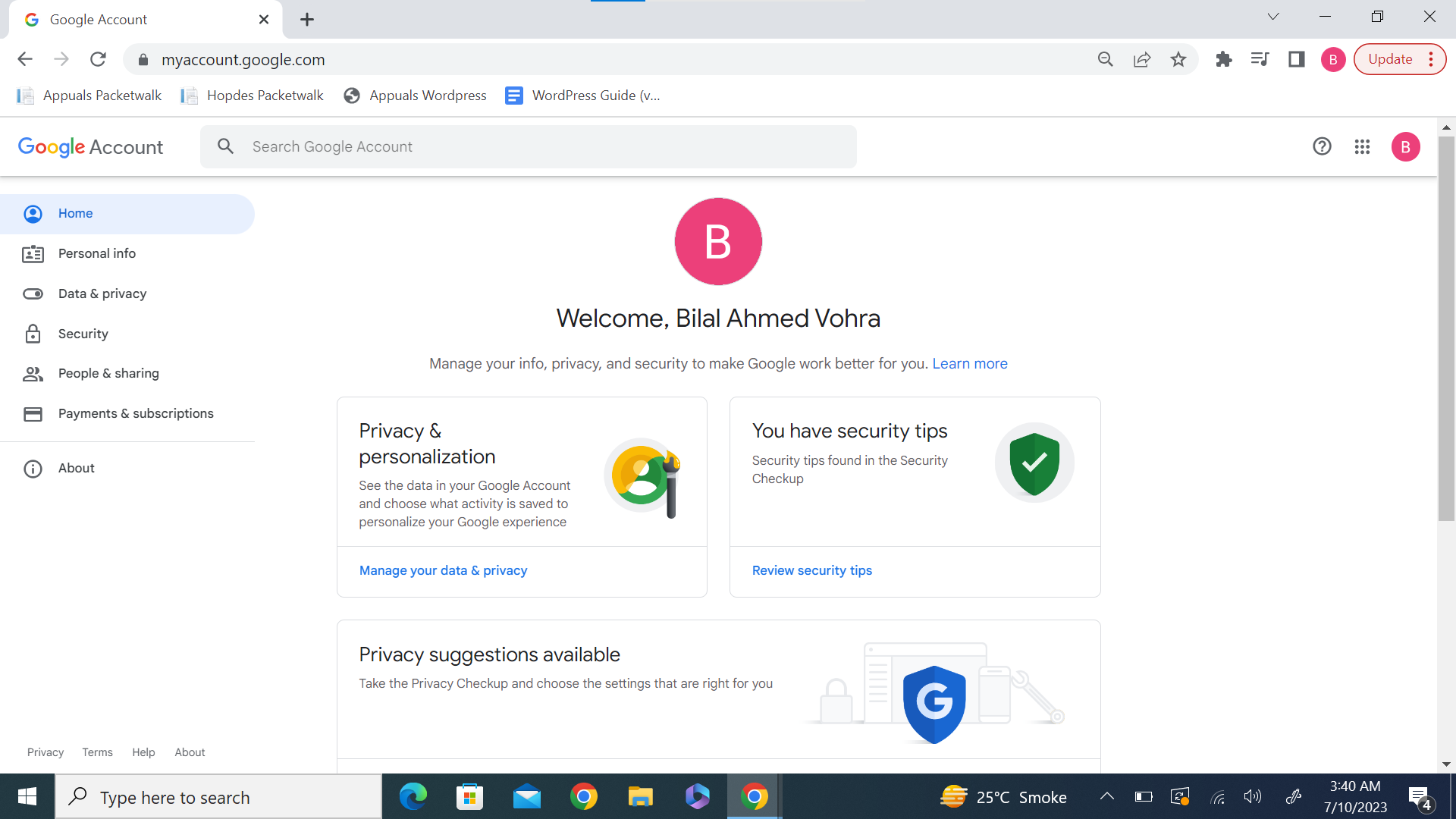
Step 2: Access Security Settings
In the column on the left side, you will see the option “Security”. Once you access this page, scroll down to where it says “Your Connections to Third-Party Apps & Services”. Next, click “See All Connections”.
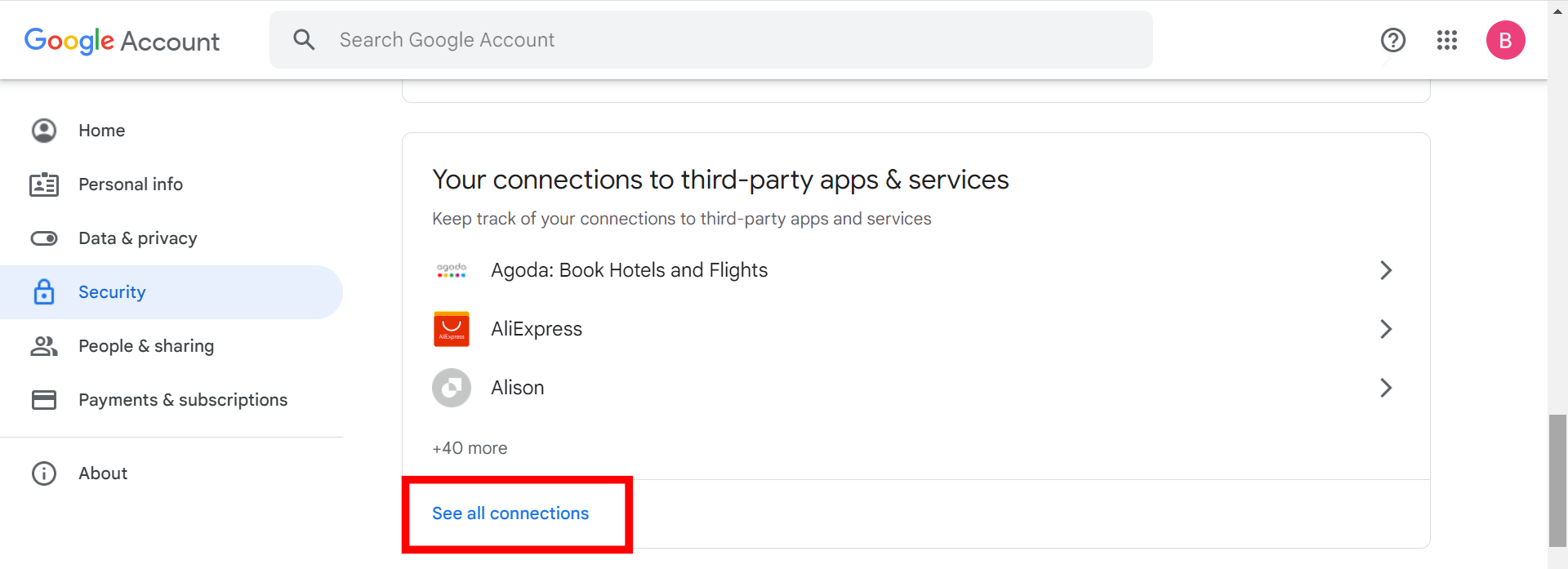
Step 3: Find the Website You Want to Remove Access From
Finding the website or application you wish to remove your Google account from is quite easy. Simply use the search bar for this purpose. you find your desired application, click on the arrow pointing to the right “>”.
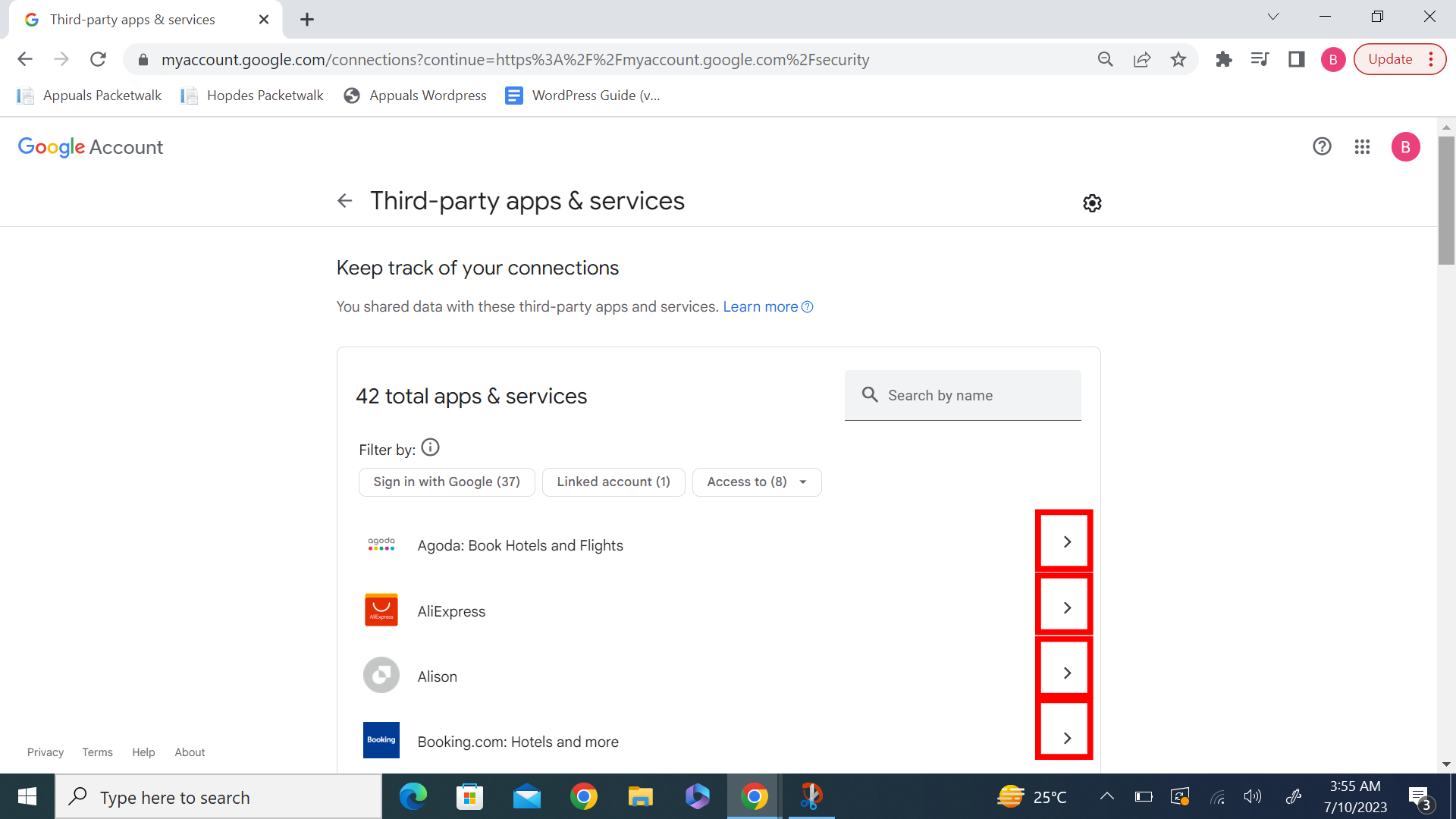
Step 4: Revoke Access
On the next screen, you will see an option that states “Delete All Your Connections” followed by the application’s name. Click this option.
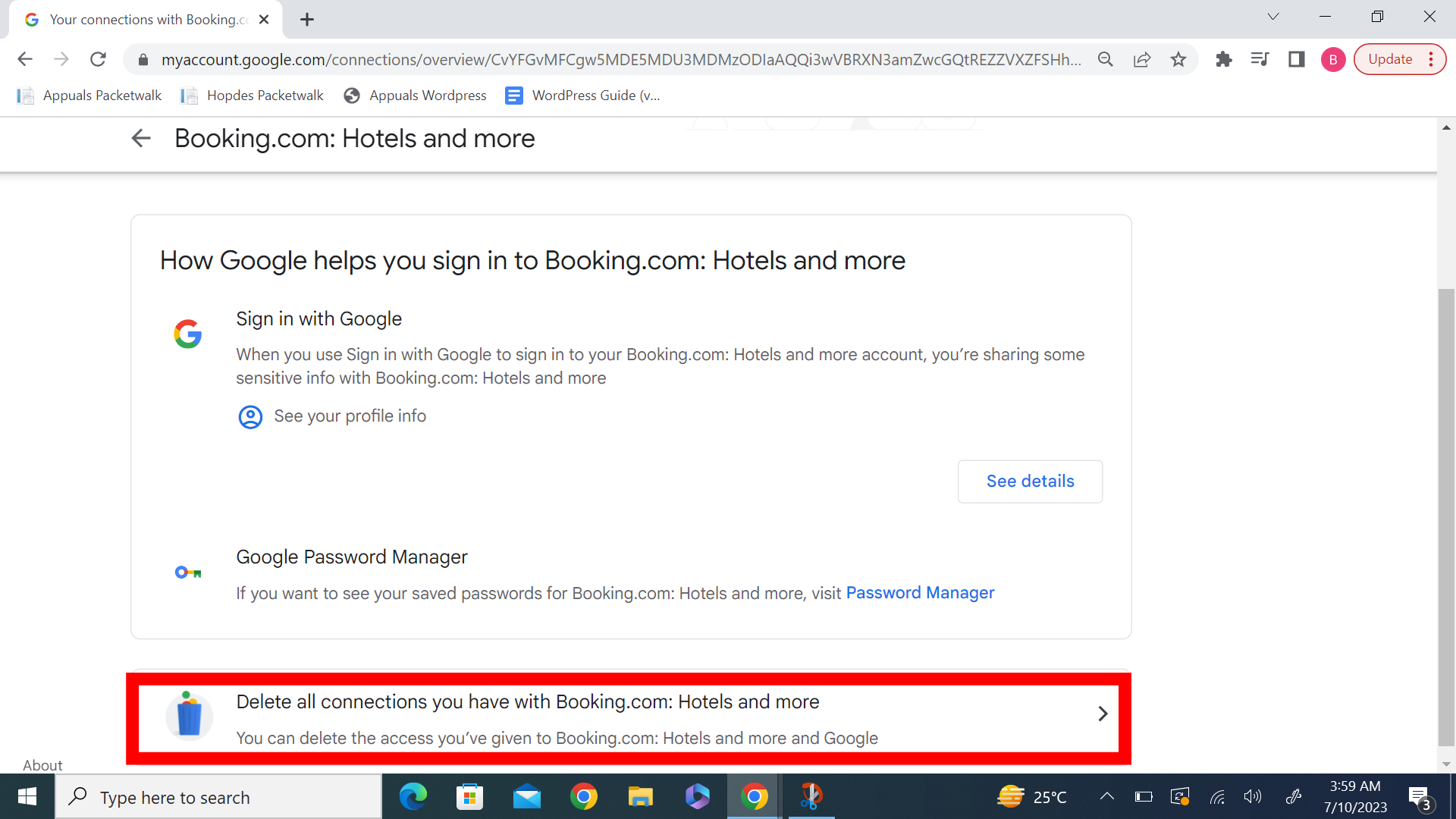
Step 5: Confirm Access Revocation
When you choose to revoke access from a website or application through Google, a prompt from Google will inform you about the implications of this decision. It will clarify that by revoking access, the website or application will no longer have permission to use your Google account. However, it’s important to note that any data previously shared with the website or application will remain intact.
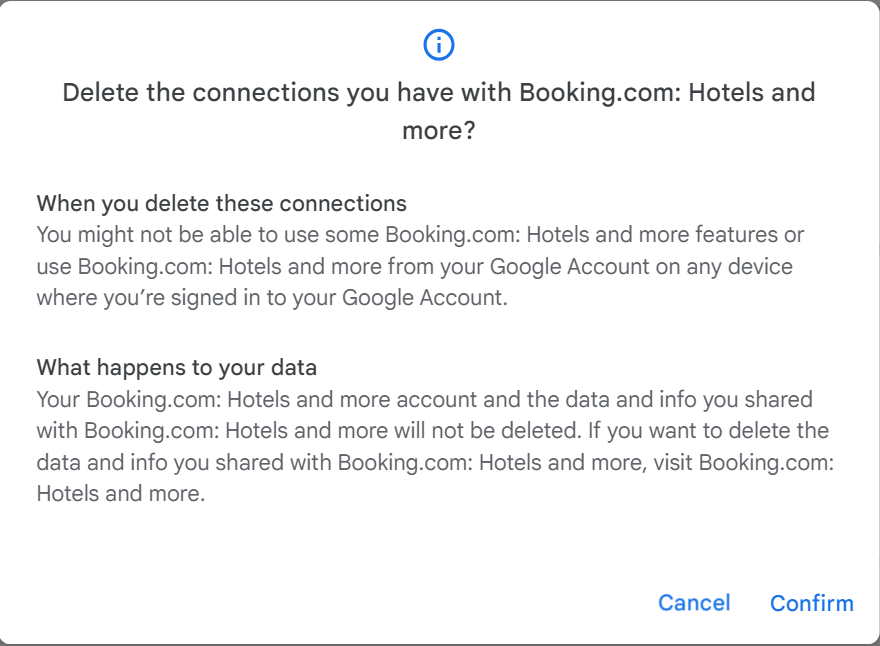
For instance, if you searched for a hotel on Booking.com while signed in with your Google account, that search history will still be associated with your Booking.com account. To remove such data, you will need to log in to the specific website’s portal and follow their data deletion process, which can vary depending on the platform.
Click on “Confirm” to proceed.
Step 6: Make a New Account on the Website
As your Google account is no longer used for access on a Non-Google website, you can now head on to the website, let’s say Airbnb, and click on “Sign Up” to make a new account. Follow the on-screen instructions from there, fill in whatever details the service asks for and verify your identify, either by phone or email, and voila! Your account should now be registered and ready to go.
Conclusion
In conclusion, logging in with Google has its benefits and drawbacks, and you should weigh them carefully before deciding how to proceed. To keep your account safe, utilize two-factor authentication and make sure you read the app’s privacy and terms of service policies before you join up.
Sign-in With Google - FAQs
Using Google Sign-In introduces risks such as data privacy concerns, security vulnerabilities, dependence on a single account, and potential for phishing attacks as well.
Google implements various security measures, including two-factor authentication, new location login notifications, mobile-based authentication, and advanced algorithms to detect and prevent unauthorized access.
Pay close attention to the URL and page design. Ensure the URL starts with “https://” and matches the official Google domain. Look for indicators like the lock icon and confirm that the page design is consistent with Google’s official login pages.
Yes, you can manage and revoke permissions granted to third-party websites by accessing your Google account settings.
 Reviewed by
Reviewed by