Enable or Disable Core Isolation Memory Integrity in Windows 11
Over the past few years, cyberattacks have evolved. Unless you’re willing to pay them money, malicious hackers can now take control of your PC and lock down files. Ransomware is the term for these assaults, which leverage kernel-level exploits to try to run malware with the greatest privileges, such as WannaCry and Petya ransomware.
To combat this, Microsoft has released a tool that lets you turn on Core Isolation and Memory Integrity to stop these kinds of attacks in order to mitigate them.
Note: Core isolation isolates the core programs in memory to shield them from malicious applications. It accomplishes this by performing those fundamental operations in a virtualized setting.
Memory integrity, sometimes referred to as Hypervisor-protected Code Integrity (HVCI), is a Windows security feature that makes it more difficult for malicious software to take control of your machine via low-level drivers. It is intended to stop malicious code from being inserted into high-security processes during assaults.
This function is available in Windows Defender Security Center. Device Security provides administration of the security features inherent in your devices, including the ability to turn features on to give heightened protection.
1. Meeting the Requirements
There are some requirements for this security feature. The hardware must also support it; it cannot only operate at the software level. Your firmware needs to handle virtualization, enabling the Windows 11/10 PC to execute apps in a container without granting them access to other system components.
Also, your device must comply with the standards for hardware security, including:
- UEFI MAT (Unified Extensible Firmware Interface Memory Memory Attributes Table)
- Secure Boot needs to be enabled.
- DEP (Data Execution Prevention)
- TPM 2.0 needs to be enabled.
- CPU Virtualization needs to be enabled.
UEFI MAT and DEP should be supported if you have a reasonably new system configuration (less than 7 years old).
However, before we explore the options available to you that will allow you to enable core isolation & memory integrity on your Windows 11 computer, you need to ensure that CPU Virtualization, TPM 2.0, and Secure Boot are enabled.
1.1. Enable CPU Virtualization
All modern AMD and Intel CPUs have a hardware feature called CPU virtualization that enables a single processor to behave as if it were several separate CPUs. This makes it possible for Windows to use the computer’s CPU power more effectively and efficiently, resulting in speedier performance.
Note: This functionality is also necessary for many virtual machine programs (like as “Hyper-V”) and must be enabled for them to function correctly or even at all.
Your computer is also able to imitate a different operating system, such as Linux or Android, thanks to CPU virtualization. You have access to a greater selection of programs to use and install on your PC when virtualization is enabled.
In our particular case, CPU isolation is needed to facilitate the smooth running of the core isolation memory integrity feature on Windows 11.
Follow the instructions below for specific instructions on how to enable CPU virtualization on your system:
- Boot the PC up and when you see the initial screen, press the dedicated key to enter the UEFI BIOS settings. It should be displayed on screen.

Access the UEFI settings Note: Check your manufacturer’s website for more instructions if you don’t see a POST screen or if it scrolls past too quickly for you to view it. You might need to read your handbook or visit your manufacturer’s website to get exact instructions because the key you hit depends on the manufacturer. Esc, Delete, F1, F2, F10, F11, or F12 are frequently used keys. Volume up and Volume down buttons are typical on tablets.
- Once you’re inside the UEFI settings, click on the Advanced tab and click on CPU Configuration from the available sub-settings.
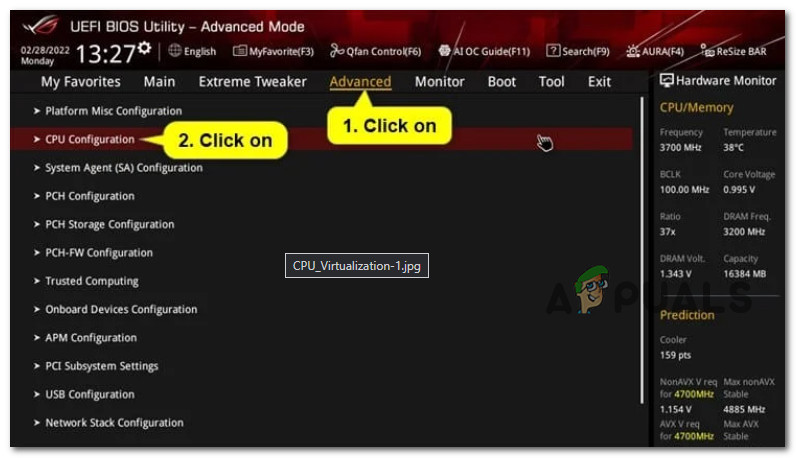
Click on CPU configuration - Depending on if you’re using an Intel or AMD CPU, perform one of the following steps:
- If you have an AMD CPU, enable the SVM Mode from the Advanced settings menu.
- If you have an Intel CPU, enable Intel (VMX) Virtualization Technology.
- Once this change is enforced, tap or click on the Exit tab, then save your changes and allow your PC to boot normally.
- After your PC boots back up, move down to the next step below to enable Secure boot.
1.2. Enable Secure Boot
Memory core isolation will need a computer that is Secure Boot capable, as we have demonstrated above.
However, there are times when a function is supported but disabled by the BIOS or UEFI settings. In these circumstances, tools like the PC Health Check might be unable to distinguish between supported and disabled features.
To ensure that computers ONLY run software approved by Original Equipment Manufacturers, the largest companies in the PC industry have agreed to an industry standard called Secure Boot (OEMs).
There is a very good probability that Secure Boot is already supported on your motherboard if it is one that is relatively recent. All you need to do in this situation is open your BIOS settings.
Here’s what you need to do to enable secure boot on your Windows 11 computer:
- Turn on your computer as usual and press the Setup (boot) key many times throughout the bootup process. Usually, you may locate it anywhere on the screen’s bottom.
Access the BIOS setup Note: The precise procedures for accomplishing this will vary depending on the manufacturer of your motherboard. Your setup key (BIOS Key) will often be one of the following: the keys F1, F2, F4, F8, F12, Esc, or Del.
IMPORTANT: To force the machine to enter the Recovery Menu if your PC by default utilizes UEFI, hold down the SHIFT key while you press the Restart button at the initial login screen. The UEFI Menu may then be accessed by selecting Troubleshoot > Advanced Options > UEFI Firmware Settings.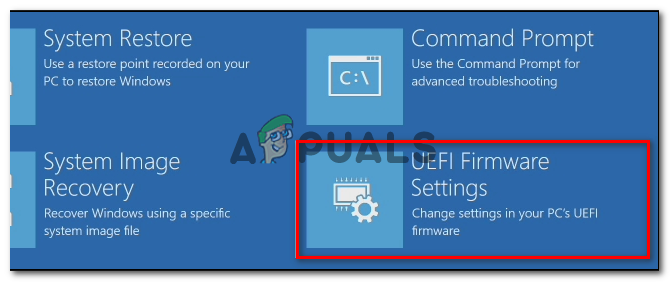
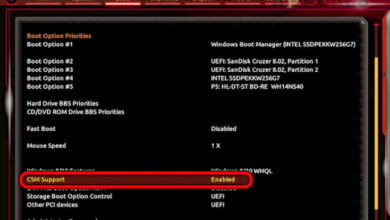
Access the UEFI Firmware settings - Once you’re in the BIOS or UEFI menu, seek for a Secure Boot option and turn it on.
Enable Secure boot Note: Depending on your motherboard manufacturer, the actual name and placement will change. Typically, you can find it under the Security tab.
- After turning on Secure Boot, save your modifications and restart your computer as usual.
- After your computer boots back up, move down to the next method below to ensure that TPM 2.0 is enabled.
1.3. Enable Trusted Platform Module 2.0
Support for TPM 2.0 is one of the unique requirements for Memory core separation in Windows 11. In your case, one of the following situations applies if TPM 2.0 is disabled:
- TPM (Trusted Platform Module) Your hardware does not support 2.0.
- The BIOS or UEFI settings on your computer have TPM 2.0 disabled.
Do the following to see whether TPM is supported by your system and whether it is turned on or off:
- To bring up the Run dialog box, press Windows key + R. After that, enter “tpm.msc” into the text field and press Enter to launch Windows 11’s Trusted Platform Module (TPM) Management pane.
Access the TPM component - Once within the TPM module, choose Status from the TPM menu’s right-hand area.
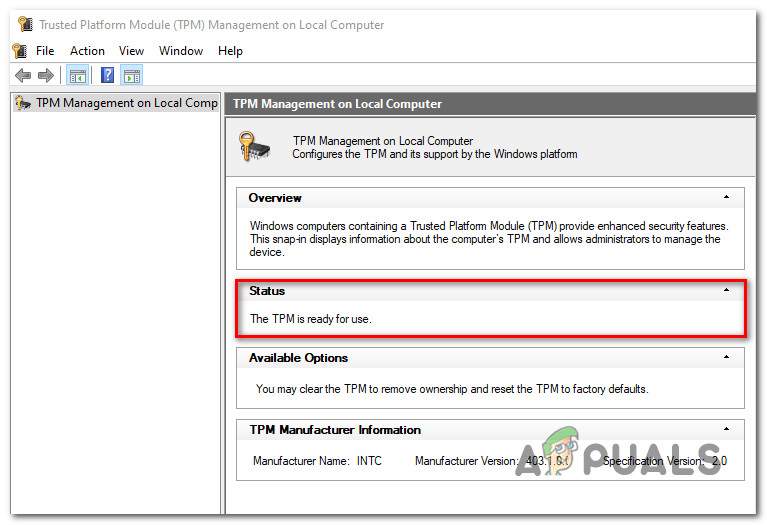
Status of TPM • If the TPM status reads “TPM is ready for usage,” TPM 2.0 is already activated and no further action is needed.
• If the TPM status reads “TPM is not supported,” your motherboard isn’t compatible with this technology. You won’t be able to install Windows 11 in this situation.
• If the message “Compatible TPM cannot be found” appears next to the TPM status, it signifies that TPM is supported but not activated in your BIOS or UEFI settings.
In case the message reads as ‘Compatible TPM cannot be found‘, follow the instructions below to enable TPM 2.0 in your BIOS or UEFI settings:
- As soon as you see the first screen on your PC (or restart it if it is already on), click the Setup key (BIOS key).
Press F2 to Enter the BIOS or UEFI settings Note: The boot key is normally visible in the lower-left or right area of the screen.
- When you are in the BIOS main menu, select the Security tab from the list of choices on the ribbon bar at the top.
- After finding the item for the Trusted Platform Module, make sure it is set to Enabled.
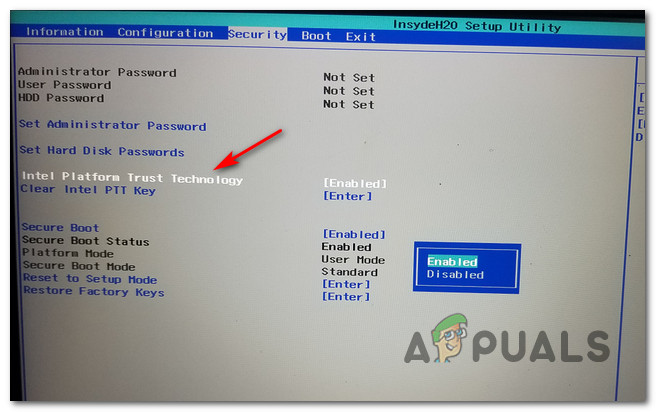
Enable the TPM component Info: The manufacturer of your motherboard will determine the precise placement of this security feature. You can find this option, for instance, as Intel Platform Trust Technology on Intel hardware.
- After making sure TPM is enabled, start your computer usually and proceed to the section after that to enable the core isolation feature on Windows 11.
2. Enable Core isolation & Memory Integrity on Windows 11
Now that all the requirements are met, it’s time to explore all the available methods that will allow you to enable core isolation & memory integrity on Windows 11.
Important: To activate or deactivate core isolation memory integrity, you must be logged in as an administrator. Also, CPU virtualization must be enabled for core isolation memory integrity.
When it comes to enabling core isolation & memory integrity on Windows 11, there are actually two different ways that will allow you to do this:
- Enable Core Isolation Memory integrity from Windows Security.
- Enable Core isolation Memory integrity via Registry Editor.
Both methods will allow you to achieve the same thing, but the way to get there is different. If you prefer using the Windows 11 GUI, go for the first option. On the other hand, if you are comfortable with using the Registry Editor, go for the second option.
2.1. Enable Core Isolation Memory Integrity via Windows Security
In Windows 11, this method is arguably the simplest method for turning on or off virtualization-based security. To put it another way, you must activate Core isolation.
In order to do this, you need to access the Device Security menu (located under Windows Security) and enable the memory integrity feature from the dedicated Core isolation details option.
Note: Our recommendation is to take the time and install any pending Windows update (cumulative, feature update and security updates) before following the instructions below.
Here’s what actions you need to perform to get this done:
- Press the Windows key + R to open up a Run dialog box. Next, type ‘windowsdefender:’ inside the run dialog box and press Ctrl + Shift + Enter to open up the Windows Defender screen with admin access.
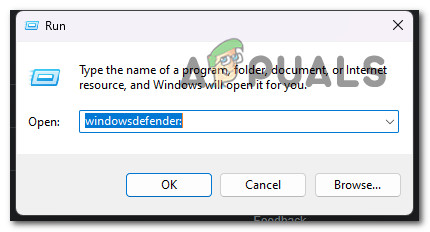
Access the Windows Defender screen - Once you’re prompted by the User Account Control (UAC), clock on Yes to grant admin access.
- After you’re inside the Windows Security tab, click on the Go to settings button associated with Device Security.
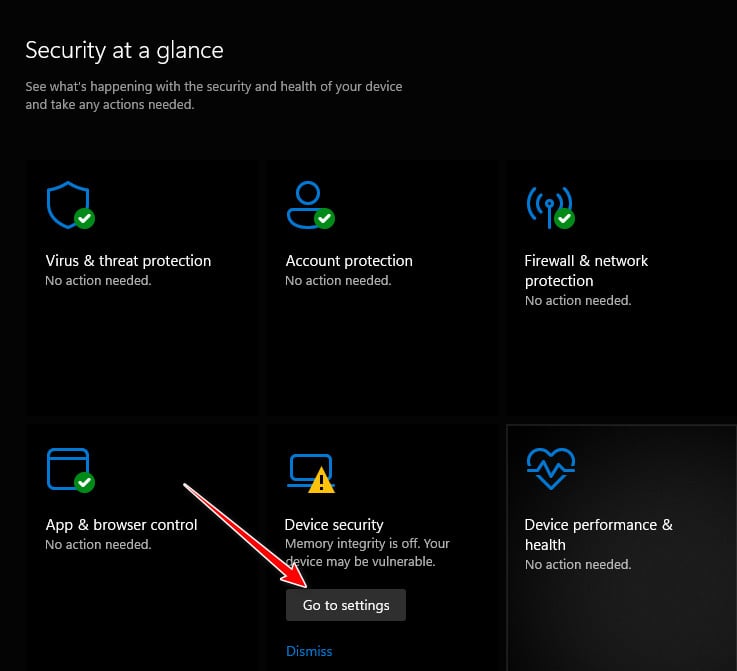
Access the Device Security Settings - From the next screen, click on Core isolation details (under Core isolation).
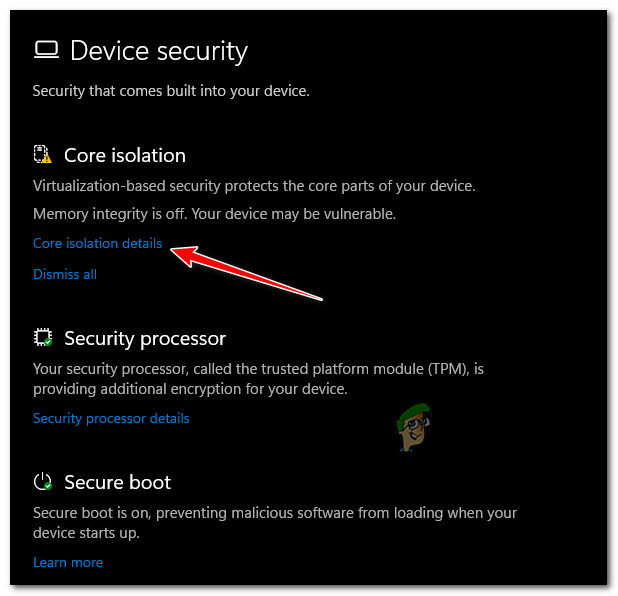
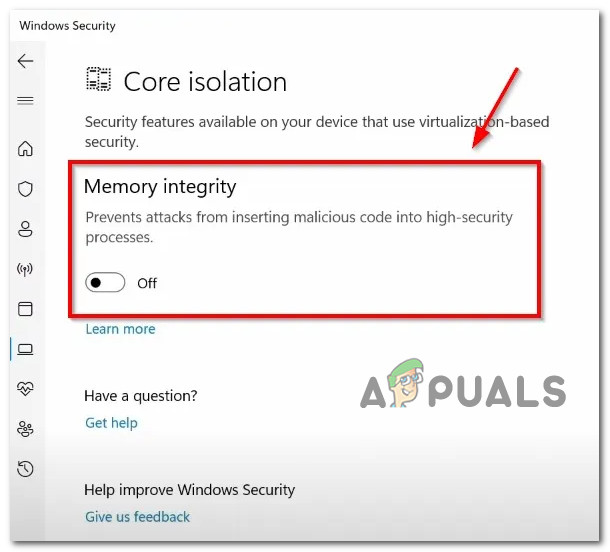
Access the core isolation details - Once you’re inside the Core isolation settings, go under Memory Integrity and enable the associated toggle.
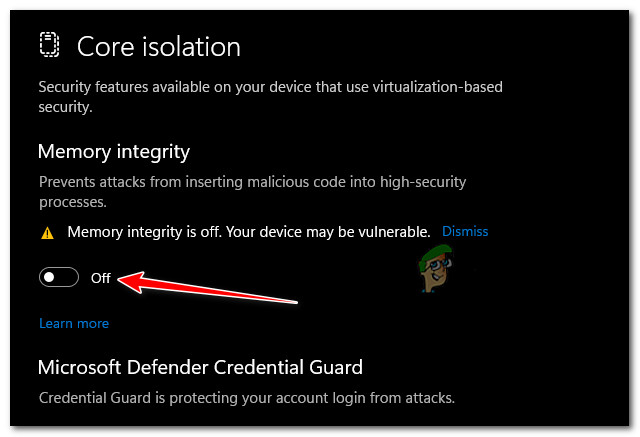
Enable Core isolation Note: You can be informed that you already have a device driver that is incompatible if memory integrity fails to turn on. Find out whether the device’s manufacturer has an updated driver by contacting them. You might be able to uninstall the device or program that utilizes the incompatible driver if they don’t have a suitable driver available. Otherwise, you can remove any drivers that are incompatible.
Note 2: The similar error could appear if you attempt to install a device with an incompatible driver after turning on memory integrity. If so, the same advice still holds true: either wait until a suitable driver is released, or check with the device manufacturer to see if they have an updated driver you can download.
- At the User Account Control (UAC), click Yes to grant admin access.
- Reboot your PC and see if the problem is now resolved.
2.1. Enable Core Isolation Memory Integrity via Registry Editor
If you are comfortable with using Registry Editor to get things done, you also have the option to enable core isolation memory integrity by modifying your Windows 11 registry.
This method involves creating a new registry value named HypervisorEnforcedCodeIntegrity under scenarios and setting the value data to before restarting your PC.
Note: Our recommendation is to take the time to back up your Registry data in advance before following the instructions below. This will allow you to quickly revert these changes in case something goes wrong during this procedure.
Follow the instructions below to enable core isolation memory Integrity via Registry Editor:
- Press Windows key + R to open up a Run dialog box.
- Next, type ‘regedit’ and press Ctrl + Shift + Enter to open up Registry Editor with admin access.
Open the Regedit utiility - If you are prompted by the User Account Control, click yes to grant admin access.
- Once you’re finally inside the Registry Editor, use the menu on the left to navigate to the following location:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\DeviceGuard\Scenarios
Note: You can either navigate to this location manually or you can paste the path above directly into the nav bar (up-top) and hit Enter to get there instantly.
- Once you arrive in the correct location, right-click on the Scenarios key and choose New > Key from the context menu that just appeared.
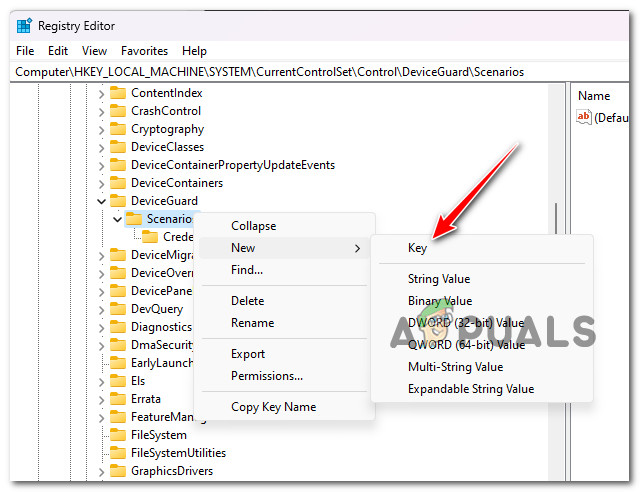
Create a new key - Name the newly created key precisely as HypervisorEnforcedCodeIntegrity and save the changes.
- Once the HypervisorEnforcedCodeIntegrity key is created, the next step is to create the DWORD that will actually enable this functionality. To do this, right-click on the newly created HypervisorEnforcedCodeIntegrity key and choose New > DWORD (32-bit) Value.
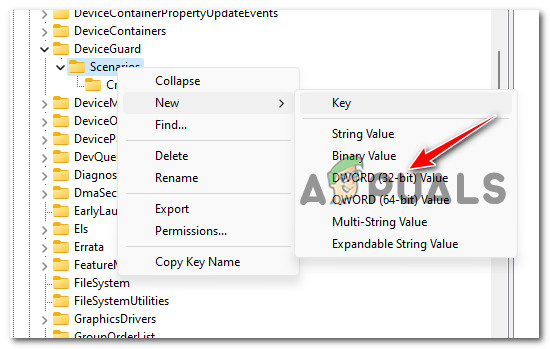
Create a new Dword - Once the new DWORD key is created, name it Enabled.
- Double-click on the newly created Enabled Dword and set the Base to Hexadecimal and the Value data to 1 before clicking Ok to save the changes.
- Close the Registry Editor and reboot your PC to allow the changes to take effect.